Security & Compliance
Built on hardware-backed security and privacy-by-design principles
Security Architecture Overview
TrustVault's security architecture is built on multiple layers of protection, from hardware-level key storage to application-level access controls.
HSM-Backed Key Protection
All cryptographic key material is generated, stored, and used exclusively within certified Hardware Security Modules (HSMs). Keys never exist in unprotected memory or storage, ensuring they remain secure even in the event of server compromise.
Our HSM infrastructure includes:
- Utimaco CryptoServer Integration: Enterprise-grade HSMs meeting FIPS 140-2 Level 3 (or equivalent) security requirements
- Hardware-Enforced Access Controls: Multi-factor authentication and role-based access control enforced at the HSM level
- Tamper-Resistant Storage: Physical and logical protections against key extraction or manipulation
- Key Backup & Recovery: Secure key backup procedures using encrypted key wrapping within trusted HSM infrastructure
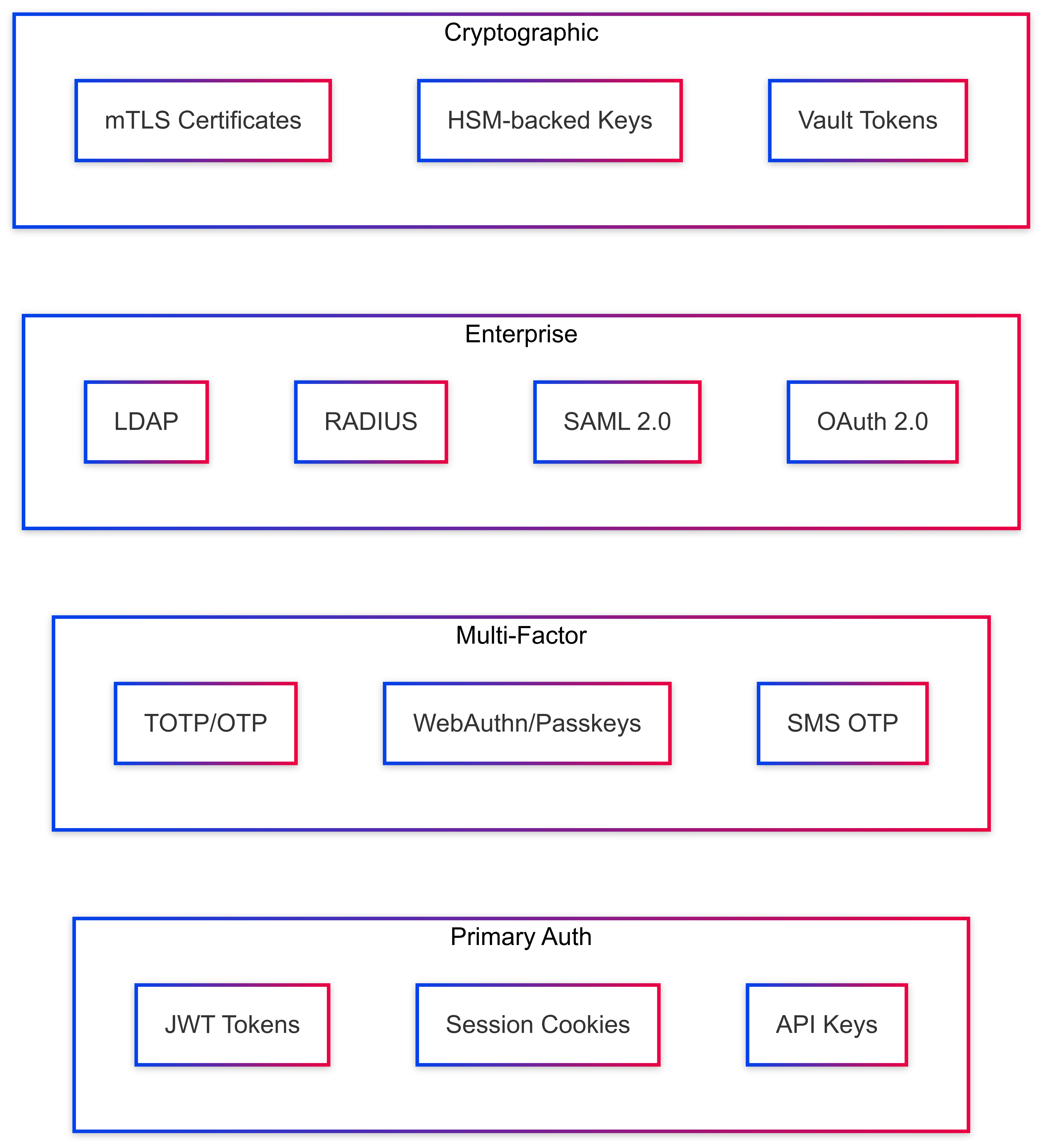
Cryptographic Authentication Architecture
Separation of Environments
TrustVault maintains strict segregation between development, pre-production, and production environments. This separation ensures:
- Testing and development activities never impact production systems
- Production cryptographic material remains isolated from non-production environments
- Separate HSM partitions and key hierarchies for each environment
- Network-level isolation with dedicated security perimeters
Access Control & Least Privilege
We implement comprehensive access controls based on the principle of least privilege:
- Role-based access control (RBAC) for all administrative functions
- Multi-factor authentication required for privileged operations
- Separation of duties for sensitive operations (e.g., key generation, CA signing)
- Regular access reviews and automated privilege expiration
Cryptography
TrustVault supports a range of modern cryptographic algorithms while maintaining the flexibility to adapt as standards evolve.
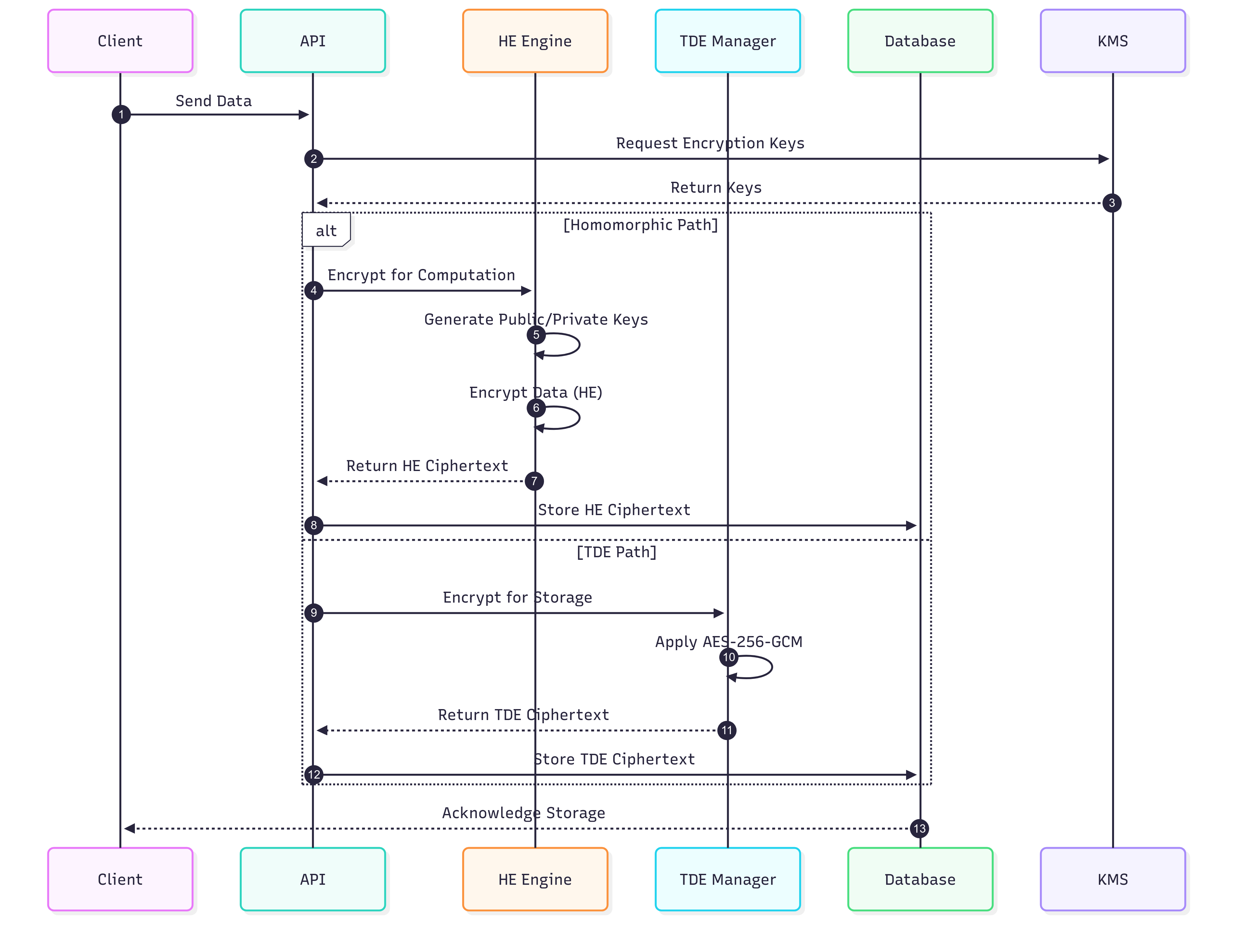
Encryption Process Architecture
Supported Algorithms
RSA: Support for 2048-bit and 4096-bit RSA keys for signatures and encryption. While RSA remains widely deployed, we recommend elliptic curve alternatives for new implementations where performance and key size are considerations.
Elliptic Curve Cryptography (ECC): Support for NIST curves including P-256, P-384, and P-521. ECC provides strong security with smaller key sizes compared to equivalent RSA strength.
Hash Functions: SHA-256, SHA-384, and SHA-512 for cryptographic hashing and message digests.
Cryptographic Agility
We recognize that cryptographic requirements change over time. TrustVault is architecturally designed to support algorithm transitions without requiring fundamental redesign:
- Post-Quantum Cryptography (PQC): Our architecture is prepared to incorporate NIST-standardized PQC algorithms (such as ML-KEM, ML-DSA, and SLH-DSA) as HSM vendors implement support
- Algorithm Negotiation: Support for multiple algorithms allows gradual migration rather than forced upgrades
- Hybrid Approaches: Capability to combine classical and post-quantum algorithms during transition periods
- Key Rotation: Automated key rotation schedules support migration to stronger algorithms over time
Data Protection & Privacy
TrustVault is designed with GDPR principles at its core, supporting data controllers and processors in meeting their regulatory obligations.
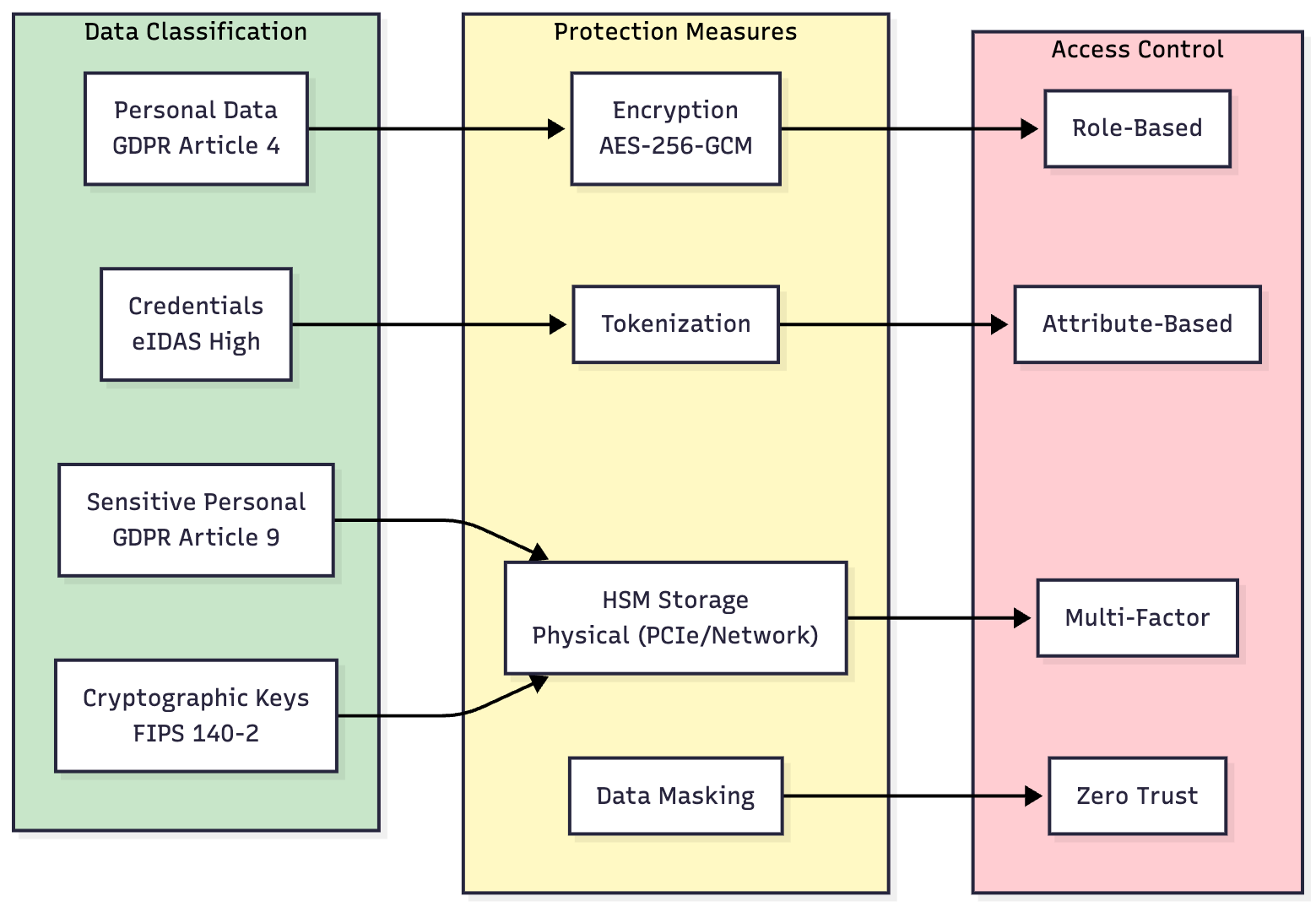
TrustVault Data Protection Framework: Classification, Protection Measures, and Access Control
Data Classification & Protection Framework
TrustVault implements a comprehensive data protection framework mapping data classifications to appropriate protection measures and access controls:
Data Classification:
- Personal Data (GDPR Article 4): General personal data subject to standard GDPR protections
- Credentials (eIDAS High): High-assurance digital credentials meeting eIDAS trust level requirements
- Sensitive Personal Data (GDPR Article 9): Special category data requiring enhanced protection (health, biometric, etc.)
- Cryptographic Keys (FIPS 140-2): Keys protected to FIPS 140-2 standards within certified HSMs
Protection Measures:
- AES-256-GCM Encryption: Personal data encrypted at rest and in transit using AES-256-GCM
- Tokenization: Credentials tokenized to reduce exposure of sensitive identity data
- HSM Storage (Physical PCIe/Network): Sensitive personal data and cryptographic keys stored in hardware security modules
- Data Masking: Production data masked in non-production environments
Access Control Mechanisms:
- Role-Based Access Control (RBAC): Applied to personal data access
- Attribute-Based Access Control (ABAC): Fine-grained access control for credentials based on attributes
- Multi-Factor Authentication (MFA): Required for accessing sensitive personal data and HSM operations
- Zero Trust Architecture: Continuous verification for all access to cryptographic materials
GDPR Principles Alignment
Our platform design aligns with the fundamental principles established in the General Data Protection Regulation:
- Lawfulness, Fairness, and Transparency: Clear processing purposes and transparent operational practices
- Purpose Limitation: Personal data processed only for specified, explicit, and legitimate purposes
- Data Minimisation: Collection limited to what is necessary for trust infrastructure operations
- Accuracy: Mechanisms to ensure personal data remains accurate and up to date
- Storage Limitation: Retention periods aligned with operational and legal requirements
- Integrity and Confidentiality: HSM-backed encryption and comprehensive security measures
- Accountability: Documentation, audit trails, and governance processes to demonstrate compliance
Role as Data Processor
Where TrustVault processes personal data on behalf of customers, we function as a data processor under GDPR. In this role:
- We process personal data only on documented instructions from the controller
- We implement appropriate technical and organizational measures to protect personal data
- We maintain records of processing activities
- We assist controllers in responding to data subject requests where feasible
- We support controllers in conducting Data Protection Impact Assessments (DPIAs) where relevant
Important: TrustVault provides technical infrastructure designed to support GDPR compliance, but does not replace the legal responsibilities of data controllers. Organizations using TrustVault remain responsible for their own compliance obligations including legal basis assessment, data subject rights, and privacy notices.
Privacy by Design
Privacy considerations are integrated into our architecture:
- Minimal processing of personal data—focusing on technical identifiers rather than personal attributes
- Support for pseudonymization and encryption of personal data
- Capability to support privacy-preserving credential architectures
- Logging and audit practices designed to balance security monitoring with privacy protection
Compliance Posture
Regulatory Alignment
TrustVault is designed to support compliance with relevant European Union regulations and standards:
- GDPR Compliance Support: Infrastructure aligned with GDPR requirements for data protection, with technical and organizational measures to support controllers and processors
- eIDAS Framework Awareness: Designed to support trust service requirements under eIDAS and emerging eIDAS 2.0 frameworks, including considerations for qualified electronic signatures, seals, and time stamps
- NIS2 Considerations: Security measures aligned with Network and Information Security Directive requirements for essential and important entities
Important Notice: TrustVault is designed to support compliance with relevant EU regulations including GDPR and, where applicable, eIDAS-related frameworks. However, we do not claim formal certifications as a qualified trust service provider or similar regulatory status unless explicitly stated. Language on this site describes capabilities, design alignment, and intended support for regulatory requirements, not certified compliance status.
Standards & Best Practices
Our infrastructure development follows recognized security and cryptographic standards:
- X.509 certificate standards (RFC 5280 and related)
- PKCS#11 for HSM integration
- KMIP for enterprise key management interoperability
- W3C standards for verifiable credentials where applicable
- NIST cryptographic guidance and recommendations
Audit & Transparency
TrustVault implements comprehensive logging and audit capabilities:
- Immutable audit logs for all cryptographic operations
- Certificate lifecycle event tracking (issuance, renewal, revocation)
- Administrative action logging with timestamp and actor identification
- Log retention aligned with operational and regulatory requirements
- Support for external audit and compliance verification processes
Questions About Our Security?
Contact us to discuss our security architecture and compliance capabilities in detail.
Contact Us